Security Awareness
Reduce human risk through training programs based on behavioral science principles, designed to deliver personalized and interactive learning experiences on cybersecurity.

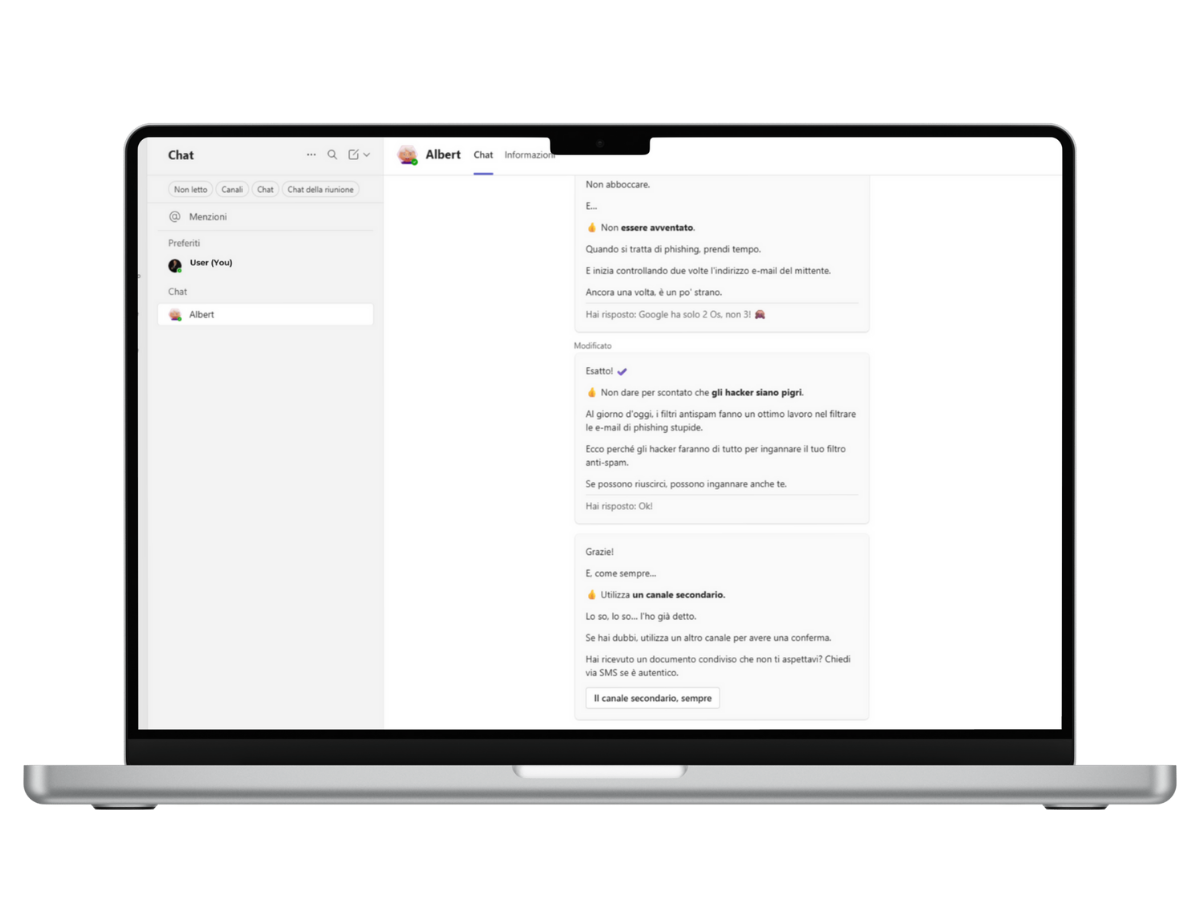
Albert, the AI assistant
Short, targeted training modules that employees can complete autonomously via chat.
Simulated attacks
Periodic phishing and social engineering tests with real-world outcomes to validate identified gaps.
Regular reportisting
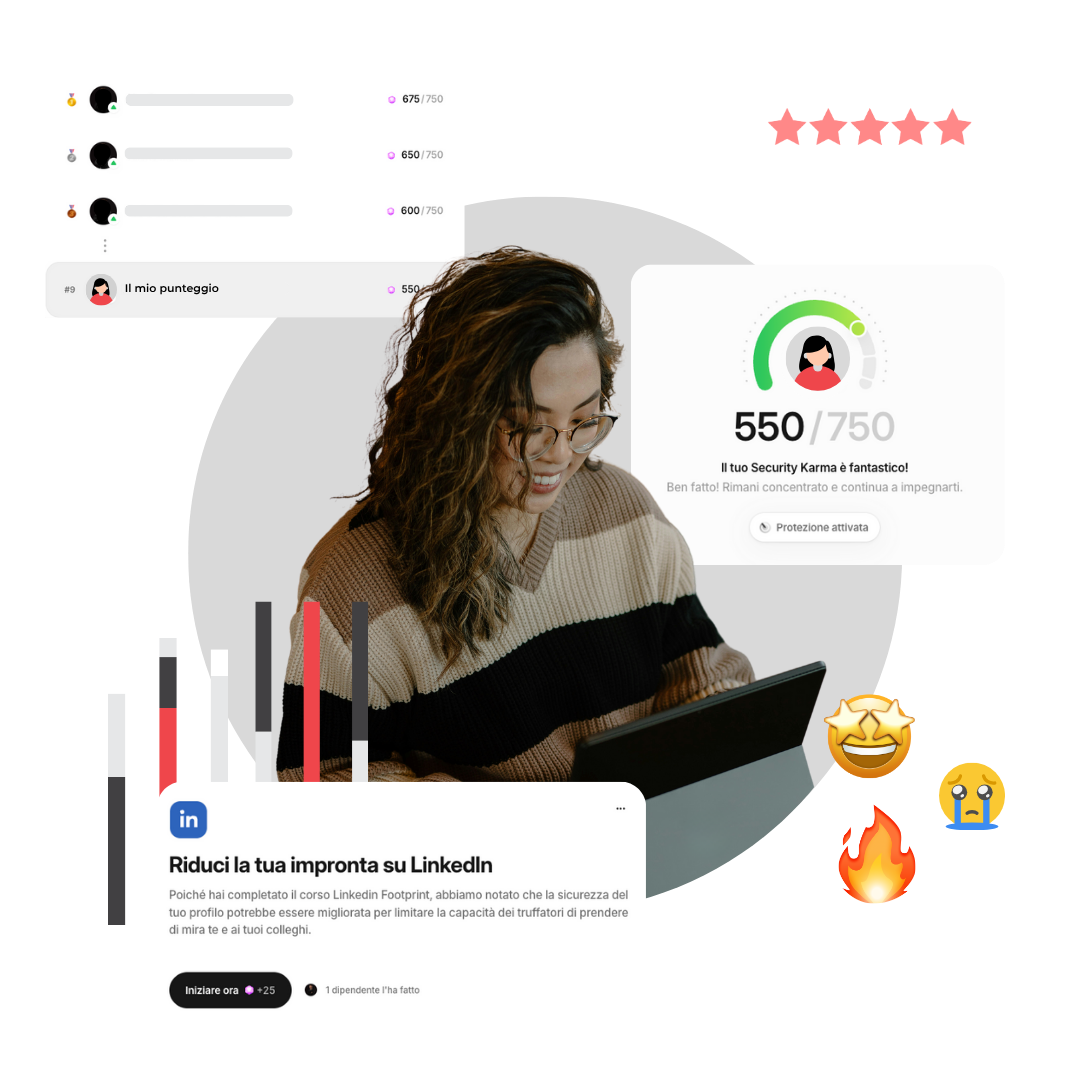
Measurement of users’ progress and identification of critical areas.
Around the
94%
of attacks starts
with phishing.
With the growing use of AI, cyberattacks targeting employees are becoming more sophisticated and harder to detect. Traditional training is not keeping pace with today’s threats. A new approach is needed.
Why choose
training
An advanced training and simulation system that teaches the recognition of real threats, turning the weak point into an active asset for the security of the entire company.
-
-50%reduction in reports of risky behavior
-
35.4%average Phish-Prone Percentage (PPP)
-
5%reduction in the click rate on malicious emails in companies
engagement
Engage and train
to reduce human risk
The platform adapts content to users’ real behaviors, delivering targeted interventions that strengthen security habits over time. Lessons are brief, relevant, and communicated in simple language, making them easy to absorb without disrupting the workday.
- Integration with Microsoft Teams
- Engaging interaction through gamification, memes, and emojis
- Optimization of training time
SIMULATION
Phishing simulations based on real user behavior
Personalized phishing simulations based on each employee’s risk profile, where frequency and difficulty levels dynamically adapt to user behavior—making the training experience more effective and targeted.
-
AI-enhanced simulations
-
Multi-channel phishing simulations


Insights
Dedicated chat
for 1:1 support
A digital assistant always available within collaboration channels, providing immediate support and contextual microlearning for daily questions and doubts.
- Simple and fast interactions
- Conversational chat
- Strengthening the security culture

From Risk to Proof: How Logs Turn Compliance into a Competitive Advantage.
When something happens to data or systems, “maybe” doesn’t count. What matters is being able to immediately prove who did what, when, with what impact and that the backups actually work.

Why data governance comes before AI
Non puoi proteggere ciò che non conosci.

AI in the enterprise: opportunity or uncontrolled risk?
Artificial intelligence is now part of everyday business life: the real crossroads is no longer whether to adopt it, but how to do so in a responsible and secure way.

MXDR with Microsoft 365: from alert to action
In security, success doesn’t come from piling up tools, but from making them communicate quickly.

Log management and SIEM: the silent heroes of cybersecurity
When it comes to cybersecurity, the focus often falls on the most well-known defense technologies: firewalls, antivirus, EDR solutions, and so on.
